A new study from Emergen Research says that the worldwide Web 3.0 industry will be worth $81.5 billion by 2030, growing at 43.7% CAGR between 2018 and 2030. According to the report, the adoption of Non-Fungible Tokens (NFTs), crypto transactions, increased transparency, and high data security are among the factors fueling the development of the global web3 market.
However, cybersecurity remains a top concern for creators, artists, and developers in the Web3 space, despite web3 developers’ primary aim to solve online privacy and data misuse issues. In recent years, numerous cases of online theft and web3 account hacks have established a threat ecosystem in the web3 space.
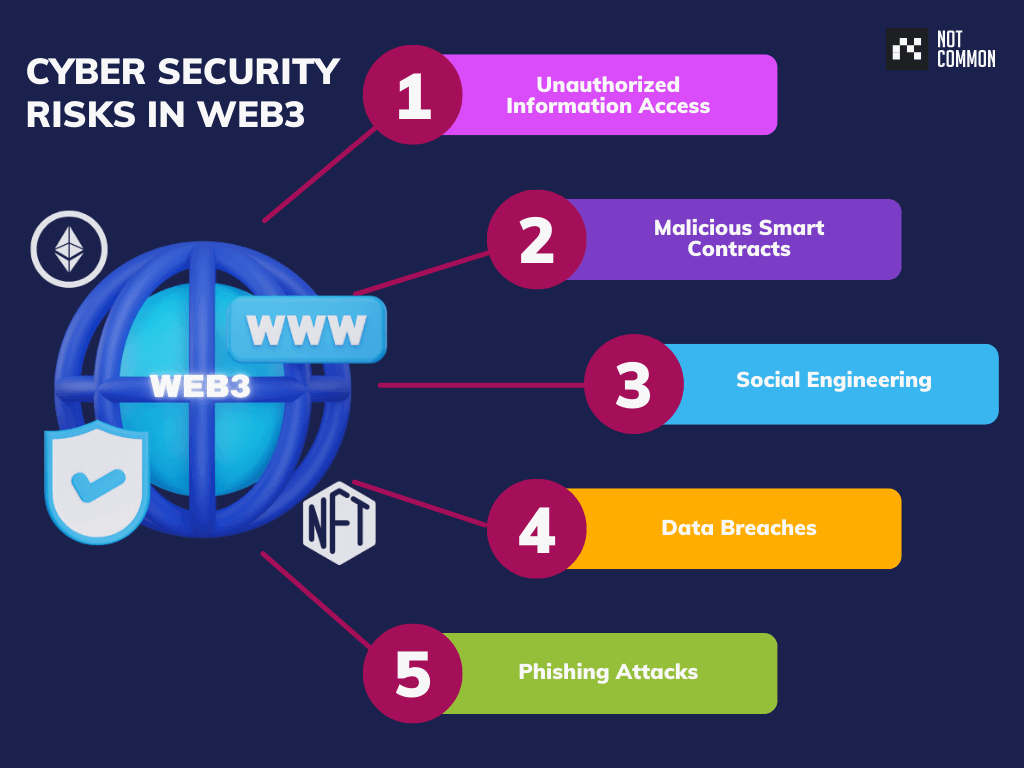
5 common cyber security risks in the web3 threat ecosystem. (Source: NotCommon)
Malicious players and hackers employ hacking techniques, including phishing, trojan horse attacks, exploiting smart contract vulnerabilities, and social media hacks to access web3 user accounts. However, one common thing among all web3 hackers is that they all want to access a web3 user’s wallet credentials or passwords and exploit it.
Thus, one cannot overstate the importance of securely storing and saving a web3 account’s seed phrase or password. Unfortunately, most web3 users need better password hygiene due to a lack of awareness and education around password(s) storage techniques.
To help our users safely navigate the developing web3 ecosystem and secure themselves against password hacks, we have curated this educational content on practical password storage and hygiene.
Why are Effective Password Storage Practices Important?
It's almost impossible to imagine a human activity that doesn't leave a digital "footprint" nowadays. However, security experts caution against using the same password for several accounts and recommend using lengthy, complex, and challenging passwords. And even if you have a strong and unique password, security experts suggest switching it frequently.
However, choosing, saving, and keeping track of dozens or even hundreds of passwords is not feasible. Particularly in the Web3 ecosystem, where account passwords are typically 12-word long seed phrases (aka recovery phrases).
Even if you take great care in creating and remembering your passwords, using them may be a hassle. You can only possibly recognize some of them, and typing them in is tedious and prone to mistakes.
Therefore, cybersecurity experts in the web3 space often recommend using effective password storage practices such as keeping a physical copy of all your passwords or using a secure open-source password manager.
Strong Passphrase vs. Complex Passwords:
If you want a secure password but don't want to use a lengthy, complicated string of random characters, there is an alternative approach. According to many security experts, the best passwords are multi-word passphrases made up of standard terms that are easy to remember. Although some people refer to these lengthy, multiple-word passwords as "pass sentences," we'll use the more popular and all-encompassing term "passphrase" in this article.
To clarify: your BIP-39-compatible crypto wallet may also include a password that you may use to access your funds. To be more precise, a BIP-39 passphrase is a string that serves as an extra layer of authentication in bitcoin wallets. Although this article focuses on passphrases in general, the BIP39 passphrase is a notable example of passphrase use that could be a password or a multi-word passphrase.
A strong password or passphrase is both lengthy and random. Longer passwords are more complex to crack than shorter ones, and this is true whether the password is a complicated string of letters or just a sequence of words.
However, in most cases, you won't be able to use a passphrase based on words rather than a complex password; the system you're trying to enter dictates the requirements for the password or passphrase it accepts. Sometimes the system may be picky about whether you use capital letters, lower-case letters, and punctuation. Therefore, the best practice is to use an easy passphrase with enough complex characters for maximum security in the web3 space.
How to Choose Strong Passphrases?
Password managers simplify creating solid and complicated passwords by allowing users to make them automatically from a pool of randomly generated characters. However, you may follow many different techniques to learn how to develop a strong passphrase.
Strong passphrases have the essential property of being stronger as word randomness increases. Even if it's seven words and 29 characters long, a traditional passphrase that you make up from standard terms (such as "I want to enjoy eggs benedict") may be highly guessable. Passphrases like "correct horse battery staple" have become popular thanks to a popular xkcd cartoon. As a result of its widespread use, this passphrase serves as a benchmark for many examinations of the passphrase security concept in vendor guidelines and academic research.
The Electronic Frontier Foundation has a word dictionary and more in-depth instructions on generating a strong password using dice if you want to learn more about safe passphrases (EFF).
Why Should You Never Reuse Passwords?
Unfortunately, hackers often steal usernames and passwords, among other valuable information, from websites they hack. Depending on the hacker's goals—monetary gain, notoriety, or mischief—they may sell the stolen data on the dark web or make it public. Once hackers make data breach public, other hackers all around the globe begin attempting to log in to several other websites using the same or slightly altered credentials, using tools to do so with remarkable speed. As a result, if you repeatedly use the same login and password for several websites, it is only a matter of time before one of these credential-stuffing assaults compromises your accounts.
This is primarily important in the web3 ecosystem, where transaction data and records are already public. If hackers end up hacking your crypto wallet, they may attempt hacking assaults on your other web3 accounts using the same credentials.
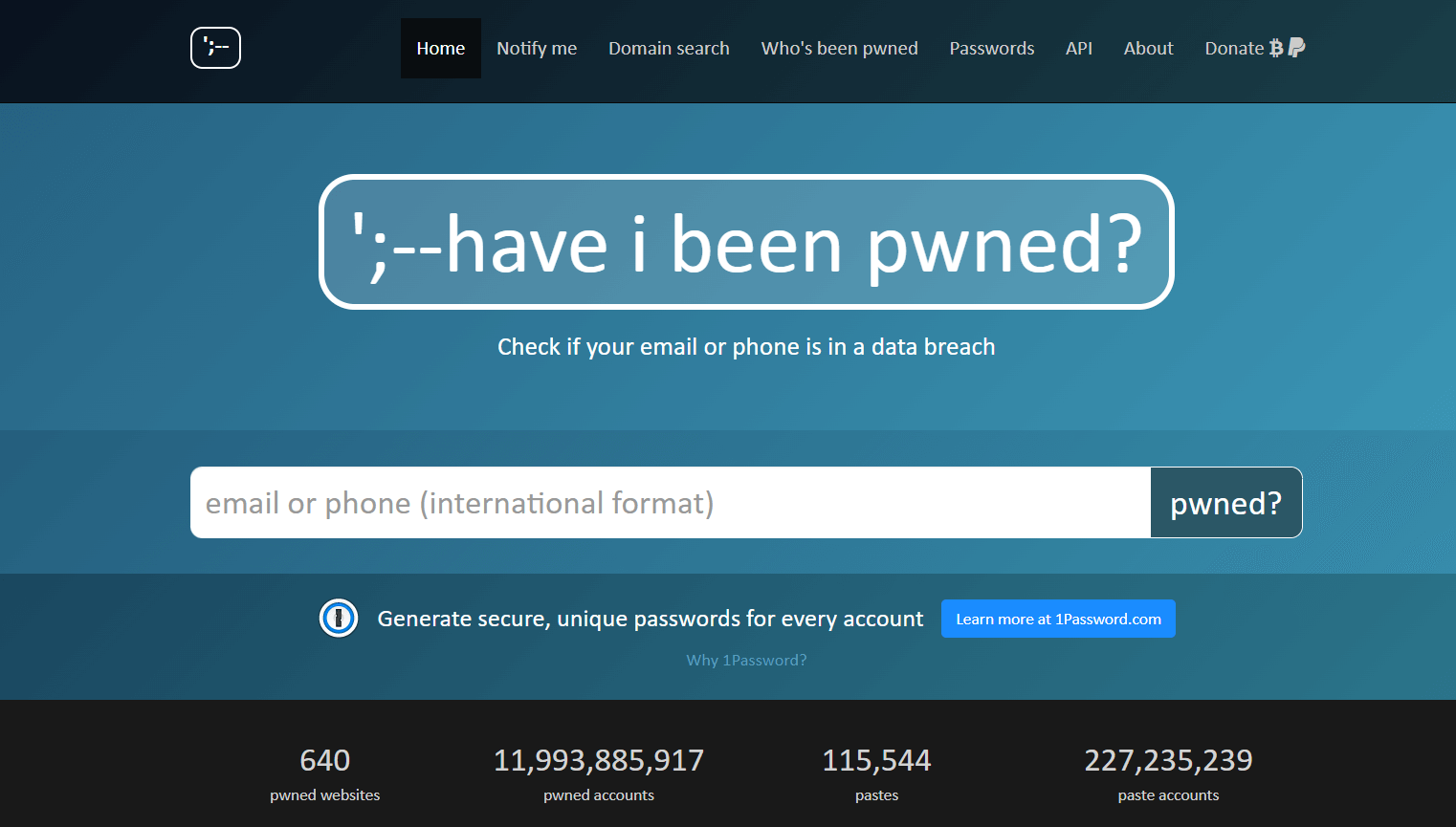
One of the best places to check an email address, phone number, or password hacking history is the security expert Troy Hunt’s haveibeenpawned website. Several password management systems are compatible with this platform, so you may feel secure that your selected passwords won't be flagged as suspect because of a past data breach.
Have-I-Been-Pawned allows you to check if your login credentials are/were part of any data breaches. (Source: haveibeenpawned)
Password managers aid you in securing your online accounts by recommending strong passwords, discouraging the reuse of passwords, and prompting you to change your passwords regularly. Because of this, using a password manager may help you maintain healthy "password hygiene."
Importance of Multi-Factor Authentication in Web3:
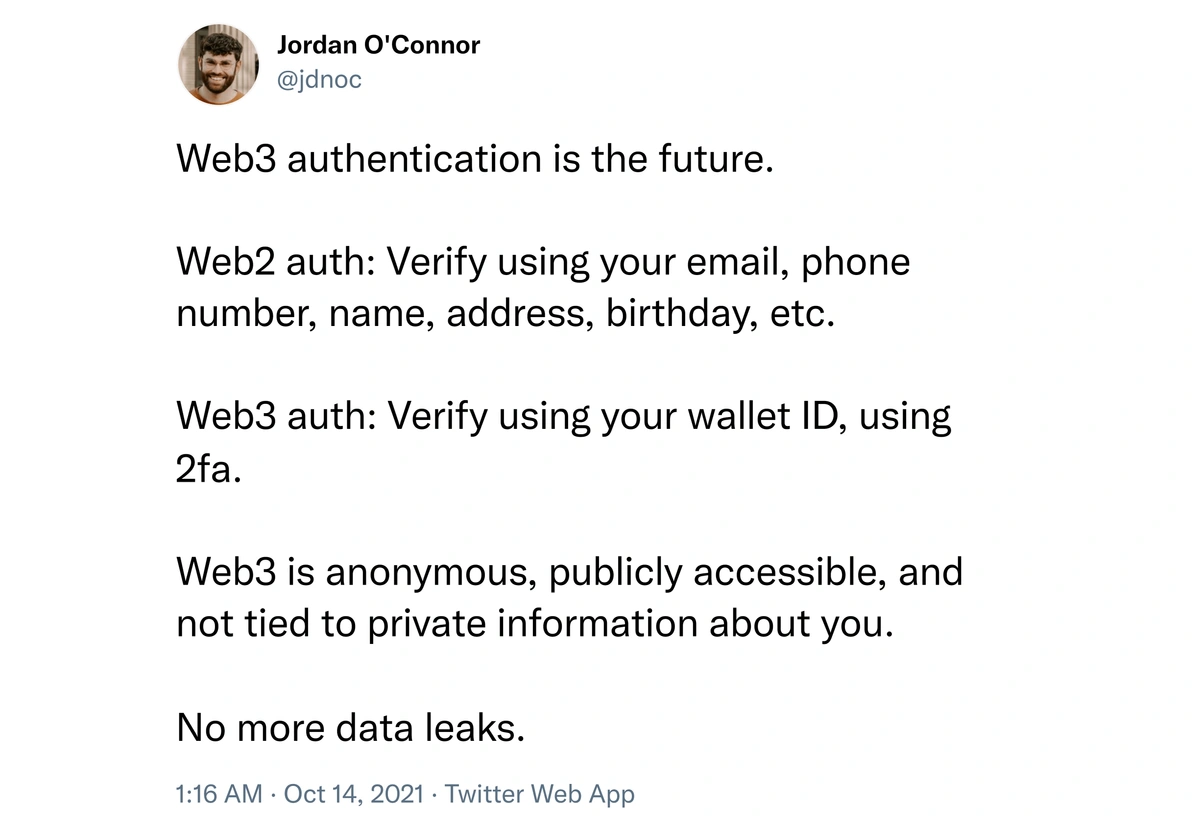
Passwords have weaknesses but are easy to use and, if chosen carefully, may be secure. However, password protection is insufficient for high-security accounts due to the risks linked to various kinds of password hacking. That's why it's common practice to use a combination of a strong password and an additional authentication method, such as 2-factor Authentication (2FA) or multi-factor Authentication (MFA), to safeguard sensitive accounts. Your web3 account is highly sensitive, as they control ownership and access to your crypto or NFT assets. Therefore, it is mandatory to enable 2FA on your web3 accounts to prevent any unauthorized access.
Enabling 2FA on your web3 accounts may save you from future data leaks. (Source: Twitter)
Multi-factor authentication is a vital element of a password manager rather than merely a convenience feature. Utilizing a password manager that supports safe authentication methods while setting it up and using it is essential. While some password managers may recommend just using the most secure authentication methods, others allow users to choose from a broader range of possibilities.
The Takeaway – Using a Password Manager to Store your Web3 Passwords
The web3 space currently has a developing threat ecosystem where hackers and malicious players use phishing to mimic popular web3 platforms. They then use these fake platforms to steal personal information from victims and get access to their accounts on legitimate services.
Many experts advise keeping all account information and seed phrases of crypto wallets separate from other credentials. Cyber security experts recommend using password managers because of the length and complexities of web3 passphrases.
To learn more about NFTs and Web3, please visit more of our articles.