Smart contracts are robust computer programs essential for adequately functioning crypto and NFT platforms on modern blockchain networks such as Ethereum. Smart contracts perform many valuable services, such as decentralization, autonomy, security, and backup of trustless crypto or NFT trading. The increasing demand for smart contracts because of the widespread use of NFT platforms makes them a tempting target for hackers and scammers, exploiting these computer programs to drain the NFT wallets of collectors.
In the last few months, NFT scammers and hackers have searched for security vulnerabilities in smart contracts that they would exploit to get into NFT platforms and marketplaces or steal valuable assets from NFT owners. However, as per the recent NFT scamming activities on Twitter and Discord, NFT hackers are now adopting a proactive approach to scamming NFT platforms. NFT hackers are no longer hunting for vulnerable smart contracts but luring collectors by sending them smart contract traps known as "honeypots."
Honeypot accounts are among the most prevalent crypto or NFT scams on Twitter, Discord, and similar platforms. If you are unaware of the many NFT honeypot scamming tactics, you expose your NFT assets to the risk of cyber theft. It has thus become mandatory to educate yourself on all types, techniques, and levels of honeypot account scams for the complete safety and security of your NFT assets.
This article will discuss the NFT honeypot account scam, one of the most common NFT scams on Twitter and Discord. We will also go through the various types and levels of the honeypot account and how it works.
What are Honeypot Accounts?
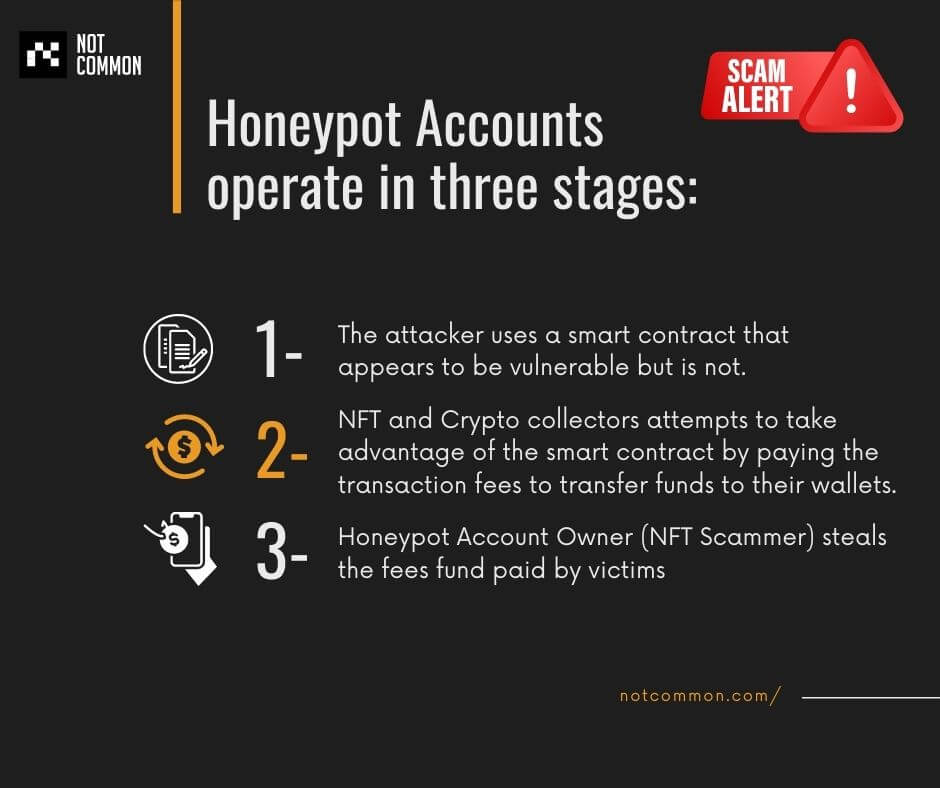
Honeypot accounts are smart contracts that appear to be defective but are not. Hackers commonly exploit such smart contracts for stealing fungible (cryptocurrency) and non-fungible tokens (NFTs) by sending a predetermined amount of cryptocurrency tokens to the smart contract. When the NFT owner or collector attempts to take advantage of this apparent vulnerability, however, a trapdoor reveals a second vulnerability that prevents the cryptocurrency from draining but instead transfers the transaction fees paid by the user to a separate smart contract.
This is a little complex and tricky, so it may quickly get confusing. Here is a simple example to help your understanding of the honeypot account scam: Consider you can earn 500 USDT if you pay 100 USDT for the transaction to process. However, when you pay the 100 USDT transaction fee, your funds are transferred to a malicious account, and you never receive the 500 USDT paid for it.
Honeypot assaults fool people because it seems like something else, much like other types of fraud. In this sense, people's greed and presumptions make it difficult to assess risk accurately. Users should fix their attention only on the glaring flaw, and they should pay no attention to the other indicators that the contract is also vulnerable. Do the laws prohibit honeypots?
Scammers establish a honeypot by making a contract appear to have a fault that it does not. This confuses the NFT collector while relying on greed to overcome common sense. Another reason that helps the malicious smart contract developers in the scam is the desire for haste.
How do Honeypot Accounts work?
In honeypot account scams, scammers lock up the user's funds in the smart contract, and only the honeypot author (scammer) can retrieve them. Typically, a honeypot operates in three phases:
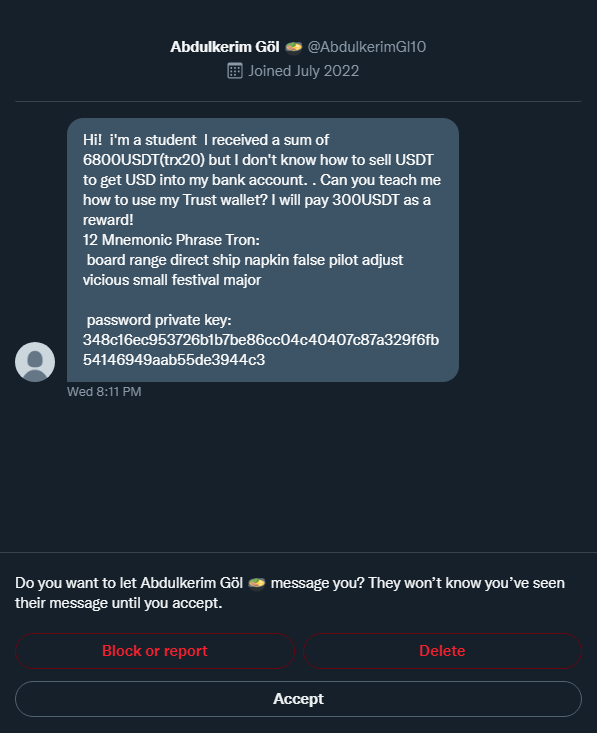
Scammers require basic knowledge of smart contracts to set up honeypots in Ethereum smart contracts. They need some tokens to set up in the smart contract and bait the smart contract to users by sending messages to NFT groups and communities. Here is an example of such statements:
Honeypot Account Bait Message (Source: Serpent)
Different Types of Honeypot Account Scams:
Honeypots may be either research or production types, with the former focusing on developing smart contracts while the latter focusing on their detection.
Research Honeypots
Research honeypots learn about and understand antagonistic behavior in the NFT or crypto ecosystem.
They learn about the patterns of attacks, security vulnerabilities, and malware types your enemies use by seeing the inside and outside of your network. Using the data from research honeypots, you can determine necessary preventive measures, critical updates, and improvement areas for your NFT or crypto project’s future.
Production Honeypots
Production honeypots, on the other hand, help identify active network intrusion and deceive the attacker. Honeypots give additional monitoring chances and fill in frequent detection gaps associated with recognizing network scans and lateral displacement; as a result, data collection remains a primary priority.
Production honeypots deliver programs that usually operate alongside other production servers in your ecosystem. Research honeypots are more complex and retain a greater variety of information types than production honeypots.
Origins of Honeypot Accounts on the Ethereum Network:
Honeypots may emerge in three separate significant projects of Ethereum smart contracts. The three levels are as follows:
Ethereum Virtual Machine (EVM)
Even though the EVM adheres to a well-established set of standards and regulations, smart contract writers can present their code in a manner that is first deceiving or misleading. These strategies might be expensive for naïve NFT collectors.
Solidity Compiler
The second area of potential for competent contract developers is the compiler. Even though specific compiler-level faults are well-documented, others might not be. These honeypots might be challenging to detect if the contract passes in real-case scenarios.
Etherscan Blockchain
The third honeypot exploits the fact that blockchain explorers give partial data. Although many individuals implicitly trust Etherscan's data, it does not necessarily provide the whole picture. Conversely, savvy smart contract developers may exploit the explorer's peculiarities.
How to Protect yourself from Honeypot Account Scams:
To protect yourself against the Honeypot Account scam, scrutinize the website of NFT or crypto projects and their social media accounts. Common honeypot account NFT projects have fake followers, likes or comments generated by bots. Similarly, if a reputable blockchain security firm does not audit a project, the NFT project could be a honeypot scam.
Honeypot Accounts typically have the following red flags:
- Dead Tokens
- No Security Audit.
- Large token wallets.
The Takeaway:
It might be surprisingly simple to fall victim to honeypot scams. The concept of rapid and simple wealth creation might appeal to everybody, but retaining a logical outlook on the market is essential.
Not all users can analyze a smart contract. For this reason, several developers give audit certifications for all blockchain-based NFT and crypto projects.
A tiny flaw in the smart contract might cause several users to lose substantial sums of money. Educating yourself against usual crypto and NFT scams is the first step to securing your assets.
To learn about other common NFT scams, follow our “Common NFT Scams” articles.